The conference proceedings are now available. Click Here.
Due to the pandemic, ACISP 2021 will be held as a virtual event.
Registration information is now available. Click Here.
About ACISP 2021
The 26th Australasian Conference on Information Security and Privacy (ACISP 2021) seeks
original papers presenting novel research results in all aspects of information security
and privacy. We welcome papers presenting theories, techniques, implementations,
applications and practical experiences on a variety of topics.
Topics of interest include, but are not limited to:
Topics of interest
- Cryptology
- Blockchain technology
- Cryptocurrency
- Post-quantum cryptography
- Authentication
- Access Control
- Key management
- Security protocols
- Privacy enhancing technologies
- Viruses and Malware
- Cloud security
- IoT security
- Software security
- Database security
- System security
- Network security
- Security policy
- Digital forensics
- Lightweight security
- Cyber-physical security
- Security implementation
Special Tracks
This year, we are organising two special tracks.-
Special Track: Blockchain
We invite papers on all aspects of Blockchain including, but not limited to:- Foundations
- New Design
- Consensus Algorithms
- Attacks on Existing Systems
- Privacy
- Scalability
-
Special Track: AI/ML Security & Privacy
We invite papers on all aspects of AI/ML Security & Privacy, but not limited to:- Foundations
- Adversarial learning
- Attacks on ML/AI systems
- Privacy Preserving Machine Learning
- Security Applications like Malware, Phishing, Anomaly detection
- Vulnerability testing
Important Deadlines
- Paper submission: February 15, 2021 February 25, 2021, 11:59pm AoE
- Notification of Acceptance: April 6, 2021 April 15, 2021
- Camera-ready Submission: April 20, 2021 May 15, 2021
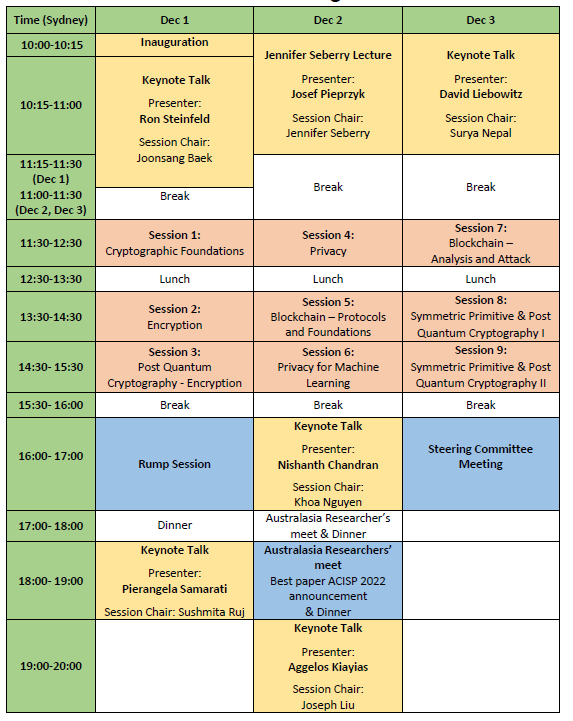
- Conference dates: July 7-9, 2021 1-3 December, 2021
Keynote Speakers

Josef Pieprzyk, CSIRO Data61, Australia
Keynote Title: Asymmetric Numeral System and Cryptography
Abstract Asymmetric numeral system (ANS) is a compression algorithm invented by Jarek Duda. Unlike the well-known Huffman compression, it works for a source with an arbitrary probability distribution of its symbols. ANS has been widely adopted by the major IT players such as Apple, Microsoft and Google. A recent explosion of Internet applications (in particular, teleconferencing) puts security of compression in the spotlight.
The presentation talks about joint compression and encryption (also called compcrypt) using ANS. We first introduce ANS and explore its mathematical and probabilistic properties. Then we show how to tweak a plain ANS to obtain a lightweight compcrypt algorithm that provides confidentiality and a low-level of integrity. The solution requires a pseudorandom bit generator (PRBG) that does not need to be cryptographically strong. We also discuss compcrypt with 128-bit security for both confidentiality and integrity. This solution applies the Keccak permutation.
Abstract Asymmetric numeral system (ANS) is a compression algorithm invented by Jarek Duda. Unlike the well-known Huffman compression, it works for a source with an arbitrary probability distribution of its symbols. ANS has been widely adopted by the major IT players such as Apple, Microsoft and Google. A recent explosion of Internet applications (in particular, teleconferencing) puts security of compression in the spotlight.
The presentation talks about joint compression and encryption (also called compcrypt) using ANS. We first introduce ANS and explore its mathematical and probabilistic properties. Then we show how to tweak a plain ANS to obtain a lightweight compcrypt algorithm that provides confidentiality and a low-level of integrity. The solution requires a pseudorandom bit generator (PRBG) that does not need to be cryptographically strong. We also discuss compcrypt with 128-bit security for both confidentiality and integrity. This solution applies the Keccak permutation.
Ron Steinfeld, Monash University, Australia
Keynote Title: Practical Lattice-Based Zero-Knowledge Proofs and
Applications
Abstract We discuss some recent developments in design and analysis of practical lattice-based zero-knowledge proofs (ZKP) and their applications. In particular, we review research challenges of Schnorr-like ZKPs in the lattice setting and in particular the progress on efficient lattice-based Schnorr-like proofs for important non-linear polynomial relations, such as binary/range proofs and one-out-of-many proofs. We also discuss recent work on applications and optimization of such proof systems as building blocks for practical advanced cryptographic protocols such as ring signatures and privacy-preserving blockchain cryptocurrency payment protocols.
Abstract We discuss some recent developments in design and analysis of practical lattice-based zero-knowledge proofs (ZKP) and their applications. In particular, we review research challenges of Schnorr-like ZKPs in the lattice setting and in particular the progress on efficient lattice-based Schnorr-like proofs for important non-linear polynomial relations, such as binary/range proofs and one-out-of-many proofs. We also discuss recent work on applications and optimization of such proof systems as building blocks for practical advanced cryptographic protocols such as ring signatures and privacy-preserving blockchain cryptocurrency payment protocols.


Pierangela Samarati, Università degli Studi di Milano, Italy
Keynote Title: Data security and privacy in emerging
scenarios
Abstract The rapid advancements in Information and Communication Technologies (ICTs) have been greatly changing our society, with clear societal and economic benefits. Mobile technology, Cloud, Big Data, Internet of things, services and technologies that are becoming more and more pervasive and conveniently accessible, towards to the realization of a smart society. At the heart of this evolution is the ability to collect, analyze, process and share an ever-increasing amount of data, to extract knowledge for offering personalized and advanced services. A major concern, and potential obstacle, towards the full realization of such evolution is represented by security and privacy issues. I will illustrate some security and privacy issues arising in emerging scenarios, focusing on the problem of managing data while guaranteeing protection of data stored or processed by external providers.
Abstract The rapid advancements in Information and Communication Technologies (ICTs) have been greatly changing our society, with clear societal and economic benefits. Mobile technology, Cloud, Big Data, Internet of things, services and technologies that are becoming more and more pervasive and conveniently accessible, towards to the realization of a smart society. At the heart of this evolution is the ability to collect, analyze, process and share an ever-increasing amount of data, to extract knowledge for offering personalized and advanced services. A major concern, and potential obstacle, towards the full realization of such evolution is represented by security and privacy issues. I will illustrate some security and privacy issues arising in emerging scenarios, focusing on the problem of managing data while guaranteeing protection of data stored or processed by external providers.
Nishanth Chandran, Microsoft Research, India
Keynote Title: Cryptographic Techniques for Secure Inference and AI
Model Validation
Abstract Secure Inference allows model owners to provide AI inference as a service to clients with the guarantee that model owners learn nothing about the client's sensitive data while also ensuring that the clients only learn the prediction of the model on their data and nothing else. This primitive also forms the basis for Secure AI Model Validation that can enable AI vendors to test the accuracy of their models on private test datasets without exposing their models in the clear.
In this task, I will describe Microsoft's EzPC system. Through this, I will survey recent works that have enabled EzPC to be a practical and usable system for the above tasks - ranging from efficient 2-party secure computation protocols and function secret sharing techniques for ML applications, to compiler support from popular ML frameworks.
Abstract Secure Inference allows model owners to provide AI inference as a service to clients with the guarantee that model owners learn nothing about the client's sensitive data while also ensuring that the clients only learn the prediction of the model on their data and nothing else. This primitive also forms the basis for Secure AI Model Validation that can enable AI vendors to test the accuracy of their models on private test datasets without exposing their models in the clear.
In this task, I will describe Microsoft's EzPC system. Through this, I will survey recent works that have enabled EzPC to be a practical and usable system for the above tasks - ranging from efficient 2-party secure computation protocols and function secret sharing techniques for ML applications, to compiler support from popular ML frameworks.


Aggelos Kiayias, University of Edinburgh, UK
Keynote Title: Resource Based Multiparty Protocols - Decentralizing
Information Technology
Abstract The bitcoin blockchain, introduced more than a decade ago, gave the first instance of a multiparty protocol that maintains its security via the incentive driven participation of a fluctuating set of resource holders. This raises the question whether it can be possible to realise any multiparty functionality out of the self-interest of computer node operators who enroll themselves to support the system’s operation in exchange of rewards that are provided in the system’s digital currency. In this talk we cast this as a general paradigm for designing and deploying multiparty protocols. We give two examples of this paradigm: the Ouroboros protocol as deployed in the Cardano blockchain and the Nym Mix-net. We discuss design challenges, solutions and open questions as well as we look at what lies ahead in decentralizing information technology services.
Abstract The bitcoin blockchain, introduced more than a decade ago, gave the first instance of a multiparty protocol that maintains its security via the incentive driven participation of a fluctuating set of resource holders. This raises the question whether it can be possible to realise any multiparty functionality out of the self-interest of computer node operators who enroll themselves to support the system’s operation in exchange of rewards that are provided in the system’s digital currency. In this talk we cast this as a general paradigm for designing and deploying multiparty protocols. We give two examples of this paradigm: the Ouroboros protocol as deployed in the Cardano blockchain and the Nym Mix-net. We discuss design challenges, solutions and open questions as well as we look at what lies ahead in decentralizing information technology services.
David Liebowitz, Penten, Australia
Keynote Title: Machine Learning for Realistic Cyber Deception
Abstract Deception is an increasingly popular cyber security technology that uses fakes IT assets to discover intrusion and data theft. Deception can also trick intruders into revealing their intent and tools. The key to successful deception and its security benefits is the realism of the assets. This talk looks at recent work on building realistic fakes by learning from real data and their application in cyber deception.
Abstract Deception is an increasingly popular cyber security technology that uses fakes IT assets to discover intrusion and data theft. Deception can also trick intruders into revealing their intent and tools. The key to successful deception and its security benefits is the realism of the assets. This talk looks at recent work on building realistic fakes by learning from real data and their application in cyber deception.

Registration
Registration for ACISP 2021 is open now. A standard price of A$30 applies to all
registrations,
including author, non-author, student, non-student etc. At least one registration is needed
for each
accepted paper.
ACISP 2021 Online Registration Form
ACISP 2021 Online Registration Form